Security researchers have discovered that Apple's iPhone keeps track of where you go – and saves every detail of it to a secret file on the device which is then copied to the owner's computer when the two are synchronised.
The file contains the latitude and longitude of the phone's recorded coordinates along with a timestamp, meaning that anyone who stole the phone or the computer could discover details about the owner's movements using a simple program.
For some phones, there could be almost a year's worth of data stored, as the recording of data seems to have started with Apple's iOS 4 update to the phone's operating system, released in June 2010.
"Apple has made it possible for almost anybody – a jealous spouse, a private detective – with access to your phone or computer to get detailed information about where you've been," said Pete Warden, one of the researchers.
Only the iPhone records the user's location in this way, say Warden and Alasdair Allan, the data scientists who discovered the file and are presenting their findings at the Where 2.0 conference in San Francisco on Wednesday. "Alasdair has looked for similar tracking code in [Google's] Android phones and couldn't find any," said Warden. "We haven't come across any instances of other phone manufacturers doing this."
Simon Davies, director of the pressure group Privacy International, said: "This is a worrying discovery. Location is one of the most sensitive elements in anyone's life – just think where people go in the evening. The existence of that data creates a real threat to privacy. The absence of notice to users or any control option can only stem from an ignorance about privacy at the design stage."
Warden and Allan point out that the file is moved onto new devices when an old one is replaced: "Apple might have new features in mind that require a history of your location, but that's our specualtion. The fact that [the file] is transferred across [to a new iPhone or iPad] when you migrate is evidence that the data-gathering isn't accidental." But they said it does not seem to be transmitted to Apple itself.
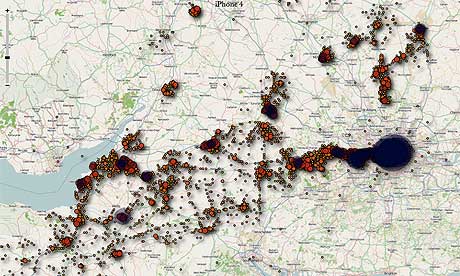 Map shows location data collected from an iPhone that had been used in the southwest of England Although mobile networks already record phones' locations, it is only available to the police and other recognised organisations following a court order under the Regulation of Investigatory Power Act. Standard phones do not record location data.
Map shows location data collected from an iPhone that had been used in the southwest of England Although mobile networks already record phones' locations, it is only available to the police and other recognised organisations following a court order under the Regulation of Investigatory Power Act. Standard phones do not record location data.
MPs in 2009 criticised the search engine giant Google for its "Latitude" system, which allowed people to enable their mobile to give out details of their location to trusted contacts. At the time MPs said that Latitude "could substantially endanger user privacy", but Google pointed out that users had to specifically choose to make their data available.
The iPhone system, by contrast, appears to record the data whether or not the user agrees. Apple declined to comment on why the file is created or whether it can be disabled.
Warden and Allan have set up a web page which answers questions about the file, and created a simple downloadable application to let Apple users check for themselves what location data the phone is retaining. The Guardian has confirmed that 3G-enabled devices including the iPad also retain the data and copy it to the owner's computer.
If someone were to steal an iPhone and "jailbreak" it, giving them direct access to the files it contains, they could extract the location database directly. Alternatively, anyone with direct access to a user's computer could run the application and see a visualisation of their movements. Encrypting data on the computer is one way to protect against it, though that still leaves the file on the phone.
Graham Cluley, senior technology consultant at the security company Sophos, said: "If the data isn't required for anything, then it shouldn't store the location. And it doesn't need to keep an archive on your machine of where you've been." He suggested that Apple might be hoping that it would yield data for future mobile advertising targeted by location, although he added: "I tend to subscribe to cockup rather than conspiracy on things like this – I don't think Apple is really trying to monitor where users are."
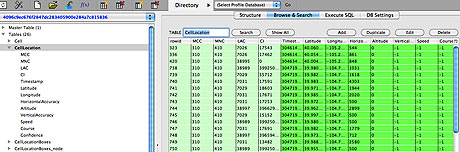 The data inside the file containing the location and time information. This is used to plot the map above The location file came to light when Warden and Allan were looking for a source of mobile data. "We'd been discussing doing a visualisation of mobile data, and while Alasdair was researching into what was available, he discovered this file. At first we weren't sure how much data was there, but after we dug further and visualised the extracted data, it became clear that there was a scary amount of detail on our movements," Warden said.
The data inside the file containing the location and time information. This is used to plot the map above The location file came to light when Warden and Allan were looking for a source of mobile data. "We'd been discussing doing a visualisation of mobile data, and while Alasdair was researching into what was available, he discovered this file. At first we weren't sure how much data was there, but after we dug further and visualised the extracted data, it became clear that there was a scary amount of detail on our movements," Warden said.
They have blogged about their discovery at O'Reilly's Radar site, noting that "why this data is stored and how Apple intends to use it — or not — are important questions that need to be explored."
The pair of data scientists have collaborated on a number of data visualisations, including a map of radiation levels in Japan for The Guardian. They are developing a Data Science Toolkit for dealing with location data.
Davies said that the discovery of the file indicated that Apple had failed to take users' privacy seriously.
Apple can legitimately claim that it has permission to collect the data: near the end of the 15,200-word terms and conditions for its iTunes program, used to synchronise with iPhones, iPods and iPads, is an 86-word paragraph about "location-based services".
It says that "Apple and our partners and licensees may collect, use, and share precise location data, including the real-time geographic location of your Apple computer or device. This location data is collected anonymously in a form that does not personally identify you and is used by Apple and our partners and licensees to provide and improve location-based products and services. For example, we may share geographic location with application providers when you opt in to their location services."
The file contains the latitude and longitude of the phone's recorded coordinates along with a timestamp, meaning that anyone who stole the phone or the computer could discover details about the owner's movements using a simple program.
For some phones, there could be almost a year's worth of data stored, as the recording of data seems to have started with Apple's iOS 4 update to the phone's operating system, released in June 2010.
"Apple has made it possible for almost anybody – a jealous spouse, a private detective – with access to your phone or computer to get detailed information about where you've been," said Pete Warden, one of the researchers.
Only the iPhone records the user's location in this way, say Warden and Alasdair Allan, the data scientists who discovered the file and are presenting their findings at the Where 2.0 conference in San Francisco on Wednesday. "Alasdair has looked for similar tracking code in [Google's] Android phones and couldn't find any," said Warden. "We haven't come across any instances of other phone manufacturers doing this."
Simon Davies, director of the pressure group Privacy International, said: "This is a worrying discovery. Location is one of the most sensitive elements in anyone's life – just think where people go in the evening. The existence of that data creates a real threat to privacy. The absence of notice to users or any control option can only stem from an ignorance about privacy at the design stage."
Warden and Allan point out that the file is moved onto new devices when an old one is replaced: "Apple might have new features in mind that require a history of your location, but that's our specualtion. The fact that [the file] is transferred across [to a new iPhone or iPad] when you migrate is evidence that the data-gathering isn't accidental." But they said it does not seem to be transmitted to Apple itself.
 Map shows location data collected from an iPhone that had been used in the southwest of England Although mobile networks already record phones' locations, it is only available to the police and other recognised organisations following a court order under the Regulation of Investigatory Power Act. Standard phones do not record location data.
Map shows location data collected from an iPhone that had been used in the southwest of England Although mobile networks already record phones' locations, it is only available to the police and other recognised organisations following a court order under the Regulation of Investigatory Power Act. Standard phones do not record location data.MPs in 2009 criticised the search engine giant Google for its "Latitude" system, which allowed people to enable their mobile to give out details of their location to trusted contacts. At the time MPs said that Latitude "could substantially endanger user privacy", but Google pointed out that users had to specifically choose to make their data available.
The iPhone system, by contrast, appears to record the data whether or not the user agrees. Apple declined to comment on why the file is created or whether it can be disabled.
Warden and Allan have set up a web page which answers questions about the file, and created a simple downloadable application to let Apple users check for themselves what location data the phone is retaining. The Guardian has confirmed that 3G-enabled devices including the iPad also retain the data and copy it to the owner's computer.
If someone were to steal an iPhone and "jailbreak" it, giving them direct access to the files it contains, they could extract the location database directly. Alternatively, anyone with direct access to a user's computer could run the application and see a visualisation of their movements. Encrypting data on the computer is one way to protect against it, though that still leaves the file on the phone.
Graham Cluley, senior technology consultant at the security company Sophos, said: "If the data isn't required for anything, then it shouldn't store the location. And it doesn't need to keep an archive on your machine of where you've been." He suggested that Apple might be hoping that it would yield data for future mobile advertising targeted by location, although he added: "I tend to subscribe to cockup rather than conspiracy on things like this – I don't think Apple is really trying to monitor where users are."
 The data inside the file containing the location and time information. This is used to plot the map above The location file came to light when Warden and Allan were looking for a source of mobile data. "We'd been discussing doing a visualisation of mobile data, and while Alasdair was researching into what was available, he discovered this file. At first we weren't sure how much data was there, but after we dug further and visualised the extracted data, it became clear that there was a scary amount of detail on our movements," Warden said.
The data inside the file containing the location and time information. This is used to plot the map above The location file came to light when Warden and Allan were looking for a source of mobile data. "We'd been discussing doing a visualisation of mobile data, and while Alasdair was researching into what was available, he discovered this file. At first we weren't sure how much data was there, but after we dug further and visualised the extracted data, it became clear that there was a scary amount of detail on our movements," Warden said.They have blogged about their discovery at O'Reilly's Radar site, noting that "why this data is stored and how Apple intends to use it — or not — are important questions that need to be explored."
The pair of data scientists have collaborated on a number of data visualisations, including a map of radiation levels in Japan for The Guardian. They are developing a Data Science Toolkit for dealing with location data.
Davies said that the discovery of the file indicated that Apple had failed to take users' privacy seriously.
Apple can legitimately claim that it has permission to collect the data: near the end of the 15,200-word terms and conditions for its iTunes program, used to synchronise with iPhones, iPods and iPads, is an 86-word paragraph about "location-based services".
It says that "Apple and our partners and licensees may collect, use, and share precise location data, including the real-time geographic location of your Apple computer or device. This location data is collected anonymously in a form that does not personally identify you and is used by Apple and our partners and licensees to provide and improve location-based products and services. For example, we may share geographic location with application providers when you opt in to their location services."
